Defend AWS Environment: DDoS Mitigation Best Practices
As more organizations move their infrastructure to the cloud, the risk of Distributed Denial of Service (DDoS) attacks grows. DDoS attacks are a form of cyberattack where an attacker overwhelms a website or application with traffic, making it unavailable to legitimate users. AWS offers a range of services to help customers protect against DDoS attacks. The AWS DDoS Resiliency Best Practices Whitepaper is an excellent resource for understanding these services and implementing best practices for DDoS resiliency.
Design a Resilient Network Architecture:
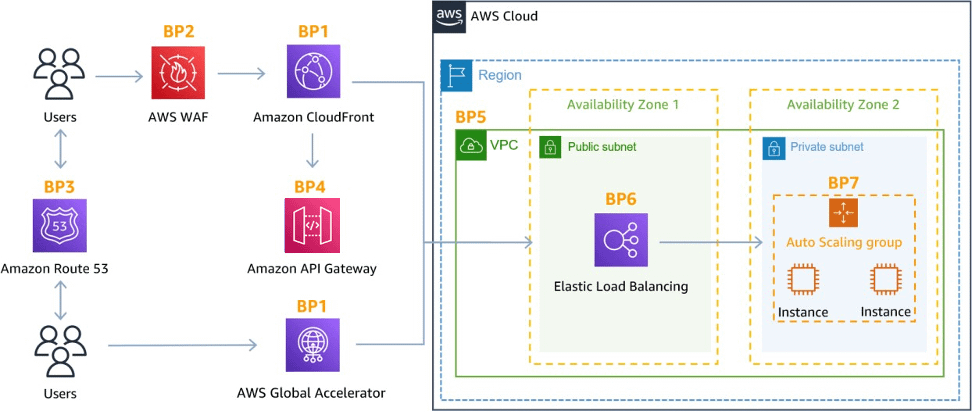
- Designing a resilient network architecture is critical for DDoS resiliency. Customers should use multiple Availability Zones to distribute resources and increase redundancy. By using AWS Global Accelerator customers can improve the availability and performance of applications by directing traffic to optimal endpoints based on geographic location, health, and routing policies. Additionally, Amazon CloudFront can be used to distribute traffic and protect against large-scale DDoS attacks. CloudFront uses a global network of edge locations to cache content and route traffic to the nearest edge location, reducing latency and improving availability.
Use Effective Traffic Management Tools:
- Effective traffic management is critical for mitigating the impact of DDoS attacks. Elastic Load Balancing (ELB) can be used to distribute traffic across multiple instances and Availability Zones. ELB provide fault tolerance and high availability. AWS WAF can filter out malicious traffic and protect against common web application vulnerabilities, including SQL injection and cross-site scripting (XSS). Amazon Route 53 can be used for DNS management and to protect against DNS-based DDoS attacks. Route 53 can also be used with ELB and CloudFront to route traffic based on latency or geographic location.
Establish a Well-Defined Incident Response Plan:
- Having a well-defined incident response plan is crucial for minimizing the impact of DDoS attacks. AWS Shield can be used to protect against common DDoS attack vectors, including network and transport layer attacks. AWS Firewall Manager can centrally manage security policies across multiple AWS accounts, making it easier to enforce security policies and respond to incidents. Amazon CloudWatch can be used to monitor for anomalous traffic and automatically trigger an incident response. Customers should establish a communication plan, define roles and responsibilities, and monitor for attacks in real-time.
Implement Multi-Layered Protection:
- Implementing multi-layered protection is an effective way to strengthen DDoS resiliency. This involves using multiple AWS services and tools in combination to create a comprehensive defense against DDoS attacks. For example, a customer could use AWS Shield to protect against common DDoS attack vectors, AWS WAF to filter out malicious traffic, and Amazon CloudFront to distribute traffic. Customers should also consider implementing additional security measures, such as network access control lists (ACLs) and security groups, to limit access to resources and reduce the attack surface.
Regularly Test and Optimize DDoS Resiliency Strategies:
- Regularly testing and optimizing DDoS resiliency strategies is critical for ensuring their are effectiveness. AWS offers a range of tools to help customers test their DDoS resiliency strategies. Amazon Inspector and AWS Config services are useful in reducing DDOS attack. Customers should also regularly review their DDoS resiliency strategies and make adjustments as necessary. For example, if a customer experiences a DDoS attack, they should review their incident response plan. We should make necessary changes to improve their defenses.
DDOS Mitigation Techniques
-
Minimize the Attack Surface Area
- This is all all about reducing the attack surface, the different Internet entry points, that allows access to your application
- Strategy to minimize the Attack surface area
- reduce the number of necessary Internet entry points,
- don’t expose back end servers,
- eliminate non-critical Internet entry points,
- separate end user traffic from management traffic,
- obfuscate necessary Internet entry points to the level that untrusted end users cannot access them, and
- decouple Internet entry points to minimize the effects of attacks.
- Benefits
- Minimizes the effective attack vectors and targets
- Less to monitor and protect
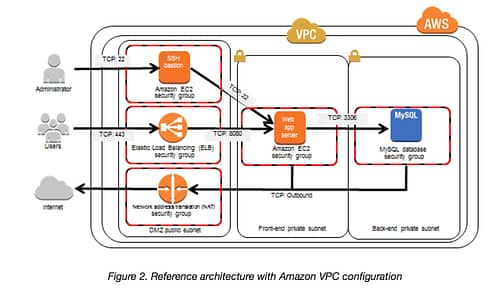
- Strategy can be achieved using AWS Virtual Private Cloud (VPC)
- helps define a logically isolated virtual network within the AWS
- provides ability to create Public & Private Subnets to launch the internet facing and non-public facing instances accordingly
- provides NAT gateway which allows instances in the private subnet to have internet access without the need to launch them in public subnets with Public IPs
- allows creation of Bastion host which can be used to connect to instances in the private subnets
- provides the ability to configure security groups for instances and NACLs for subnets, which act as a firewall, to control and limit outbound and inbound traffic
2. Be Ready to Scale to Absorb the Attack
- DDOS mainly targets to load the systems till the point they cannot handle the load and are rendered unusable.
- Scaling out Benefits
- help build a resilient architecture
- makes the attacker work harder
- gives you time to think, analyze and adapt
- AWS provided services :-
- Auto Scaling & ELB
- Horizontal scaling using Auto Scaling with ELB
- Auto Scaling allows instances to be added and removed as the demand changes
- ELB helps distribute the traffic across multiple EC2 instances while acting as a Single point of contact.
- Auto Scaling automatically registers and deregisters EC2 instances with the ELB during scale out and scale in events
- EC2 Instance
- Vertical scaling can be achieved by using appropriate EC2 instance types for e.g. EBS optimized or ones with 10 gigabyte network connectivity to handle the load
- Enhanced Networking
- Use Instances with Enhanced Networking capabilities which can provide high packet-per-second performance, low latency networking, and improved scalability
- Amazon CloudFront
- CloudFront is a CDN, acts as a proxy between end users and the Origin servers, and helps distribute content to the end users without sending traffic to the Origin servers.
- CloudFront has the inherent ability to help mitigate against both infrastructure and some application layer DDoS attacks by dispersing the traffic across multiple locations.
- AWS has multiple Internet connections for capacity and redundancy at each location, which allows it to isolate attack traffic while serving content to legitimate end users
- CloudFront also has filtering capabilities to ensure that only valid TCP connections and HTTP requests are made while dropping invalid requests. This takes the burden of handling invalid traffic (commonly used in UDP & SYN floods, and slow reads) off the origin.
- Route 53
- DDOS attacks are also targeted towards DNS, cause if the DNS is unavailable your application is effectively unavailable.
- AWS Route 53 is highly available and scalable DNS service and have capabilities to ensure access to the application even when under DDOS attack
- Shuffle Sharding – Shuffle sharding is similar to the concept of database sharding, where horizontal partitions of data are spread across separate database servers to spread load and provide redundancy. Similarly, Amazon Route 53 uses shuffle sharding to spread DNS requests over numerous PoPs, thus providing multiple paths and routes for your application
- Auto Scaling & ELB
In summary, protecting against DDoS attacks is critical for organizations operating in the cloud. By designing a resilient network architecture, using effective traffic management tools, establishing a well-defined incident response plan, implementing multi-layered protection, and regularly testing and optimizing DDoS resiliency strategies, customers can significantly improve their defenses against DDoS attacks on AWS.
Further Reading




3 Comments
Pingback:
Pingback:
Pingback: